Phishing & scam emails - How can I tell?
Phishing emails are cybersecurity attacks via email that appear to be legitimate but are actually sent from malicious third-parties.
They may be attempting to steal:
- Your identity
- Authentication details (your username and password)
- Credit card information
- Other personal information, such as your address, phone numbers, date of birth, license and passport numbers etc
The purpose of this document is to help you to know the techniques that can be used to tell the difference between a legitimate email and a phishing scam.
Consider the following example email:
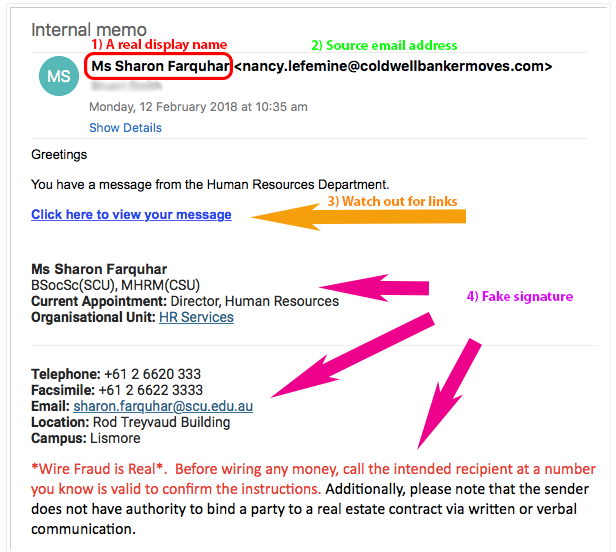
Don't trust the display name for a sender
In the above example, the display name (circled in red) is displayed as Sharon Farquhar from HR. Never trust the text here. A favourite tactic of scammers is to put something in here that will deceive people into thinking the sender is trustworthy, in this case, the director of HR, Southern Cross University. The presence of Sharon's name here in our example does not indicate that the email came from Sharon, nor that Sharon's account is compromised in any way.
Examine the email address of the sender
While this technique is not always perfect, it will assist you to identify 80% or more of scam emails. In the above example, the sender's actual email address is underlined in green. This does not match Sharon's staff email address at all, and thus should be treated with suspicion. All SCU email addresses should end in @scu.edu.au (staff) or @student.scu.edu.au. If they do not: you can be sure its a scam.
There are techniques to hide the sender's actual address and substitute the display of a fake address that seems OK, so we've included more techniques to assist you further.
Links in emails
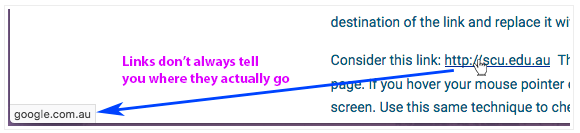
A good general rule is to avoid clicking links in emails whenever possible, even if you trust the sender. A common technique that is used is to hide the actual destination of the link and replace it with something that looks safe.
Consider this link: http://scu.edu.au The display name appears to be the trusted university website. But if you click on it, you'll find yourself at a google search page. If you hover your mouse pointer over the link (but don't click), the actual destination link is often displayed in the status bar at the very bottom of the screen (see screenshot below). Use this same technique to check links in emails.
If it looks strange, don't click! Forward the email to the Service Desk for further confirmation.
If you follow a link, and it goes to a login screen: instead of putting your real username and password in, try entering a known fake username and password. What happens? do you get a "invalid username or password" error? The absence of these errors is a likely indicator of deceptive intent.
Don't believe everything you see
In our example above, the signature used by the attackers is a copy 'n' paste of the university staff directory. The details are correct, but the method of display does not 'look' like an email signature. If a signature looks strange, then you should try to verify the email is authentic with the sender (ie, via phone, text message, or in person).
Consider the following points:
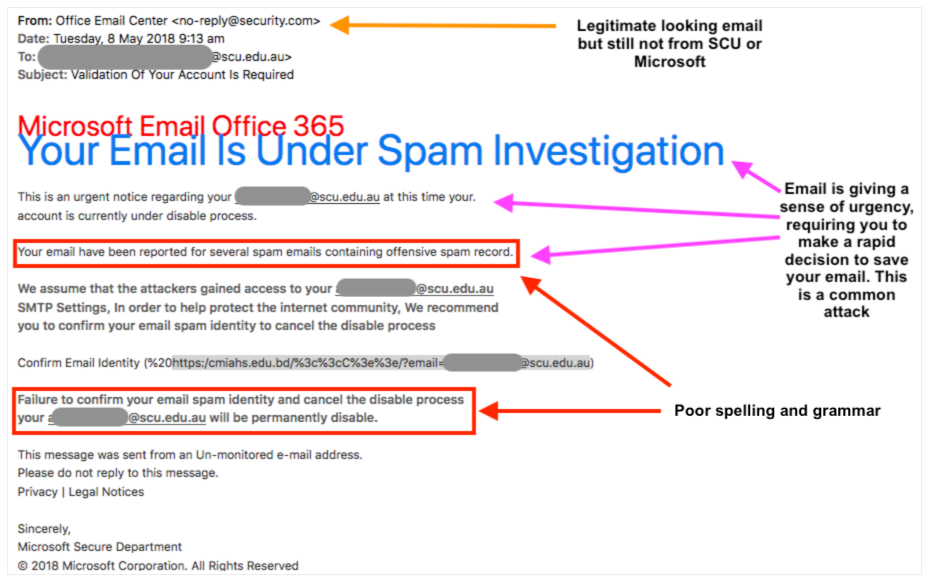
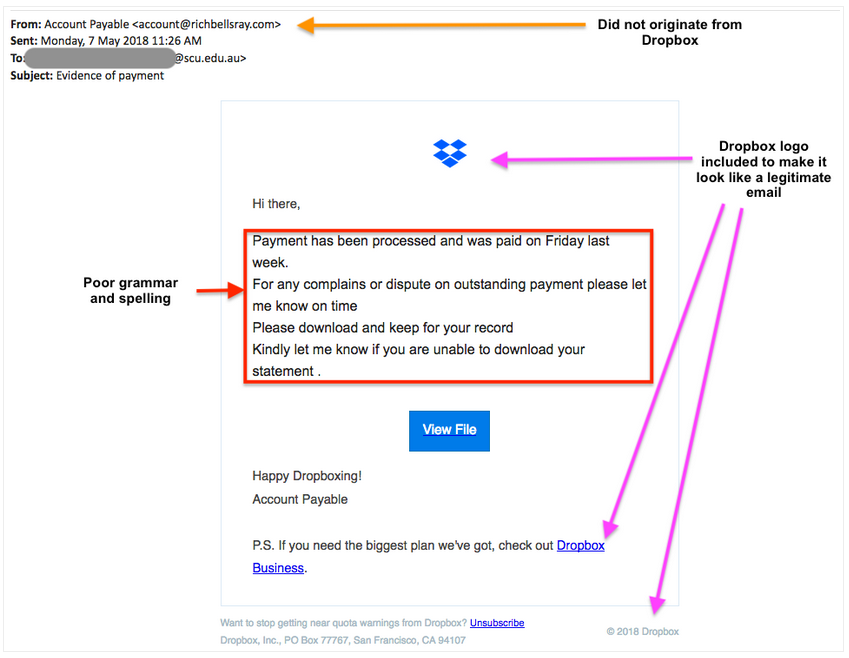
- Is the spelling and grammar correct? - Often English is not a primary language for the hackers, so they don't have great spelling and grammar. Its often very easy to tell a scam on this point alone.
- Is the email encouraging urgency? - "Your account is suspended", "Your email box is full", "Your refund is about to expire". The hackers are encouraging an impulse decision, they don't want you to think about the possibility that you're being deceived or that what your doing is strange.
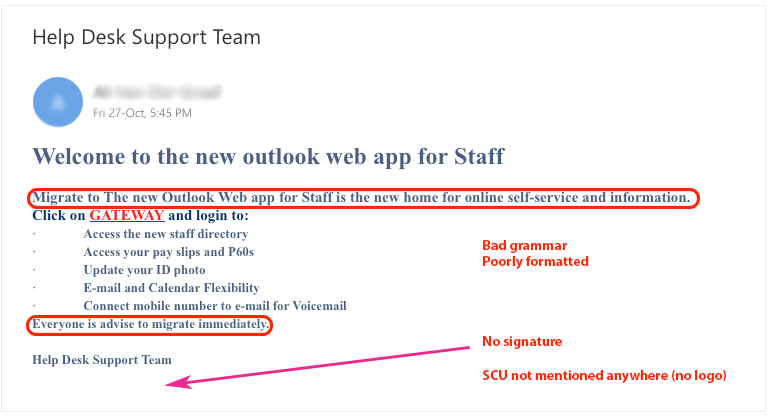
- Does the email look well formatted? - Often hackers don't bother to format the emails and/or web pages in a well structured way. Additionally, they will try using the same email across many campaigns, so they don't want to use a single institutional logo.
- Does the email look 'OK'? - If a request seems strange, or doesn't follow the normal procedures: you should assume its fraudulent until you can confirm otherwise. Some known fraudulent techniques:
- Is the email asking you to change bank details?
- Are they requesting you send credit card details over email?
- Is it asking for your email/MySCU credentials on a login screen that doesn't look normal?
- Fraud warnings/virus scans/privacy statements at the bottom - The presence of a footer containing a fraud warning/virus scan/privacy statement etc is not proof that an email is safe. Often attackers put these in to 'lower your guard'. Consider the example at the top of this article.
Examples
Example 1 - This email was harvesting email login credentials.
Example 2 - This email was harvesting email login credentials.
Example 3 - This email was attempting to get the victim to install malware via a link